The vulnerability lies in the use of parseObject(search).
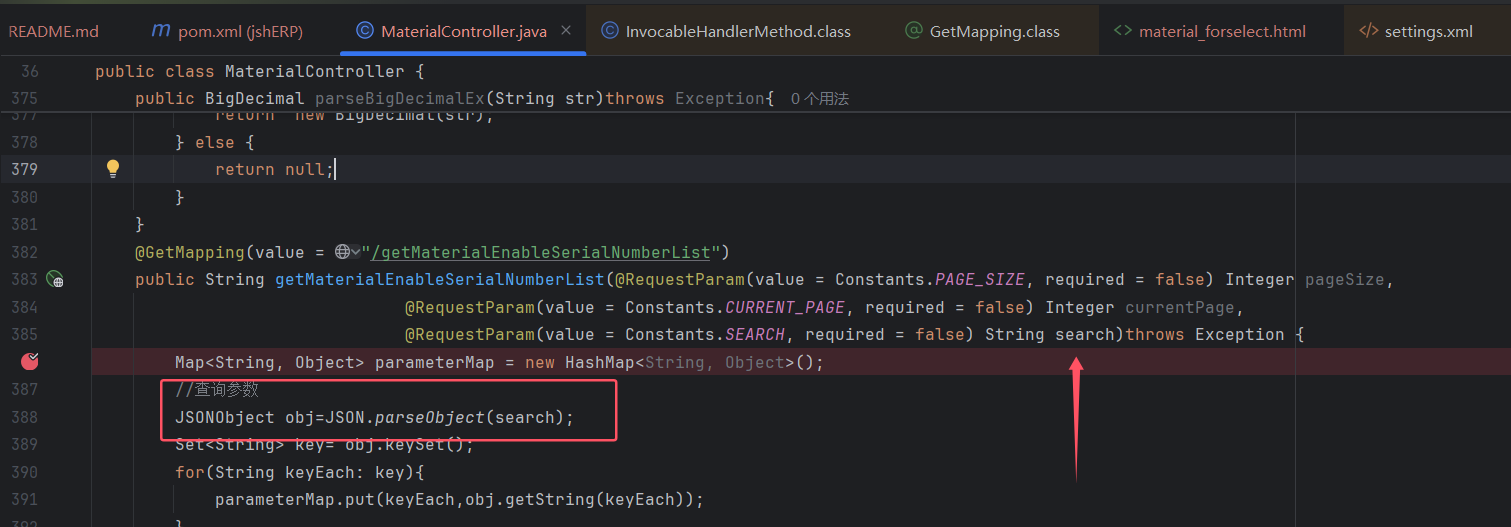
The search parameter is controllable, allowing for a deserialization attack, as shown below:

The payload used in the search parameter is as follows:
1 | json复制编辑{ |
The vulnerability lies in the use of parseObject(search).

The search parameter is controllable, allowing for a deserialization attack, as shown below:

The payload used in the search parameter is as follows:
1 | json复制编辑{ |